Welcome to the Yeti documentation site!


Yeti aims to bridge the gap between CTI and DFIR practitioners by providing a Forensics Intelligence platform and pipeline for DFIR teams. It was born out of frustration of having to answer the question “where have I seen this artifact before?” or “how do I search for IOCs related to this threat (or all threats?) in my timeline?”
What is Yeti?
In a nutshell, Yeti allows you to:
- Store and manage Forensics Intelligence: DFIQ objects, forensic artifact definitions, Sigma and Yara rules, reusable queries, etc.
- Bulk search observables and get a pretty good guess on the nature of the threat, and how to find it on a system.
- Inversely, focus on a threat and quickly list all TTPs, malware, and related forensic artifacts.
- Let CTI analysts focus on adding intelligence rather than worrying about machine-readable export formats.
- Easily incorporate your own data sources, analytics, and logic.
This is done by:
- Storing technical and tactical CTI (observables, TTPs, campaigns, etc.) from internal or external systems.
- Being a backend for DFIR-related queries: Yara signatures, Sigma rules, DFIQ.
- Providing a web API to automate queries (think incident management platform) and enrichment (think malware sandbox).
- Export the data in user-defined formats so that they can be ingested by third-party applications (SIEM, DFIR platforms).
Some screenshots
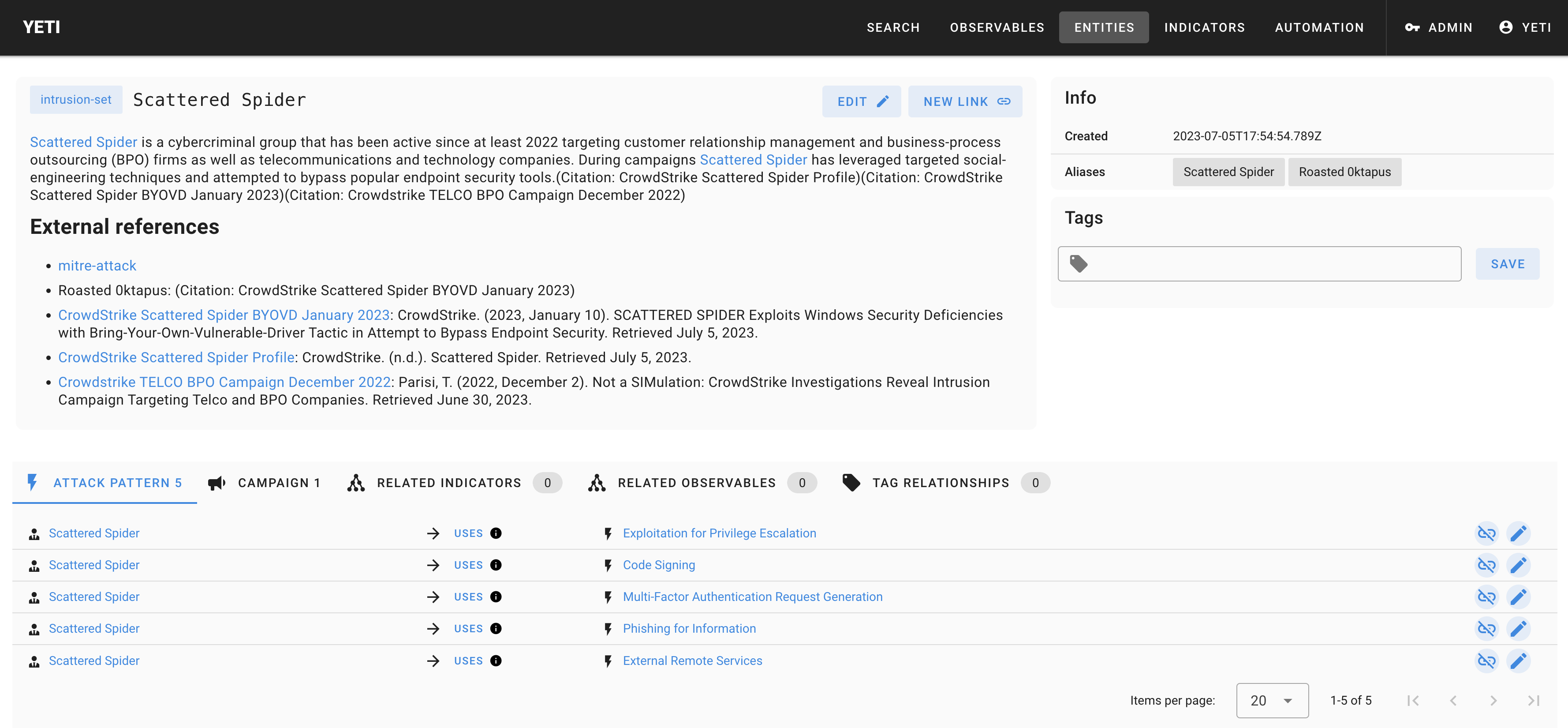
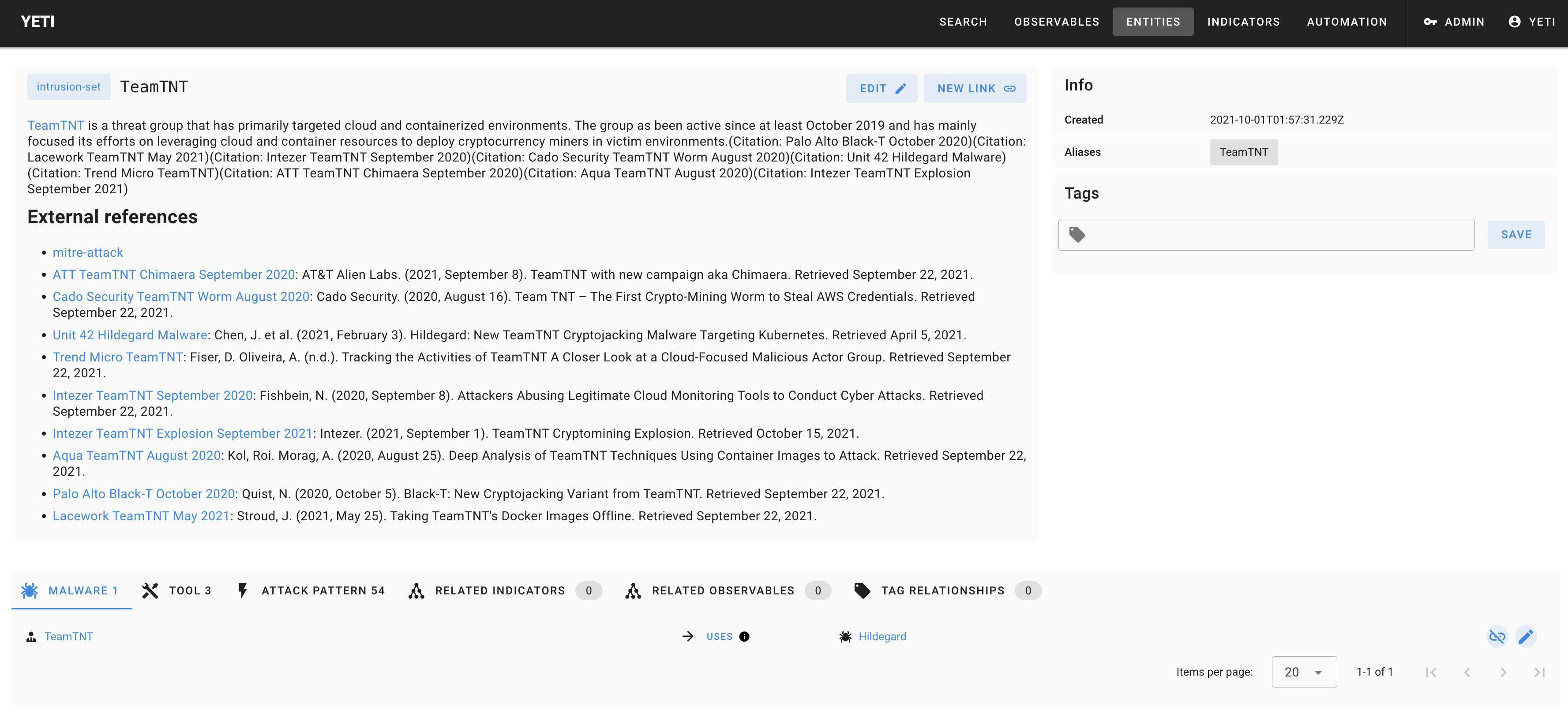
Example of ScatteredSpider as imported through MITRE ATT&CK
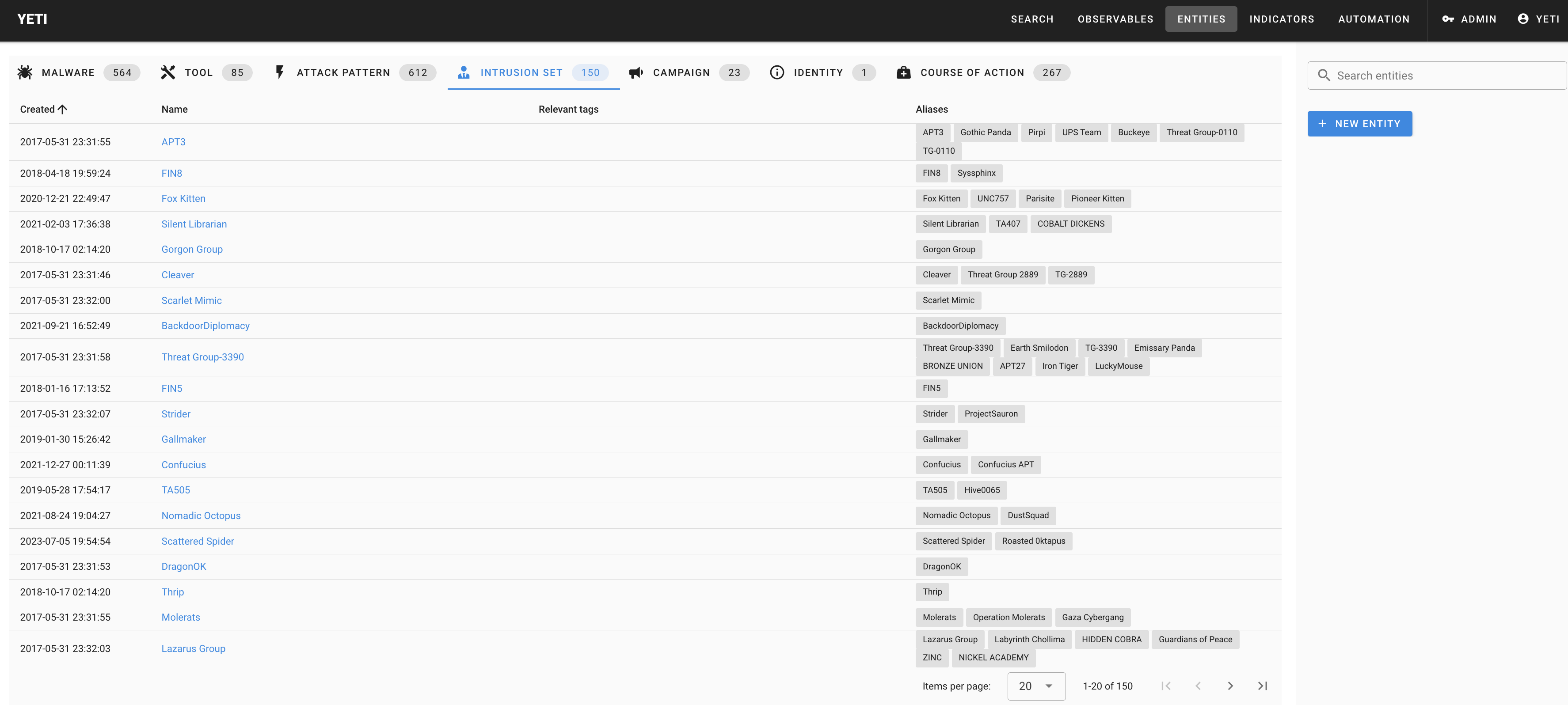
Example: Intrusion sets as imported through the MITRE ATT&CK feed
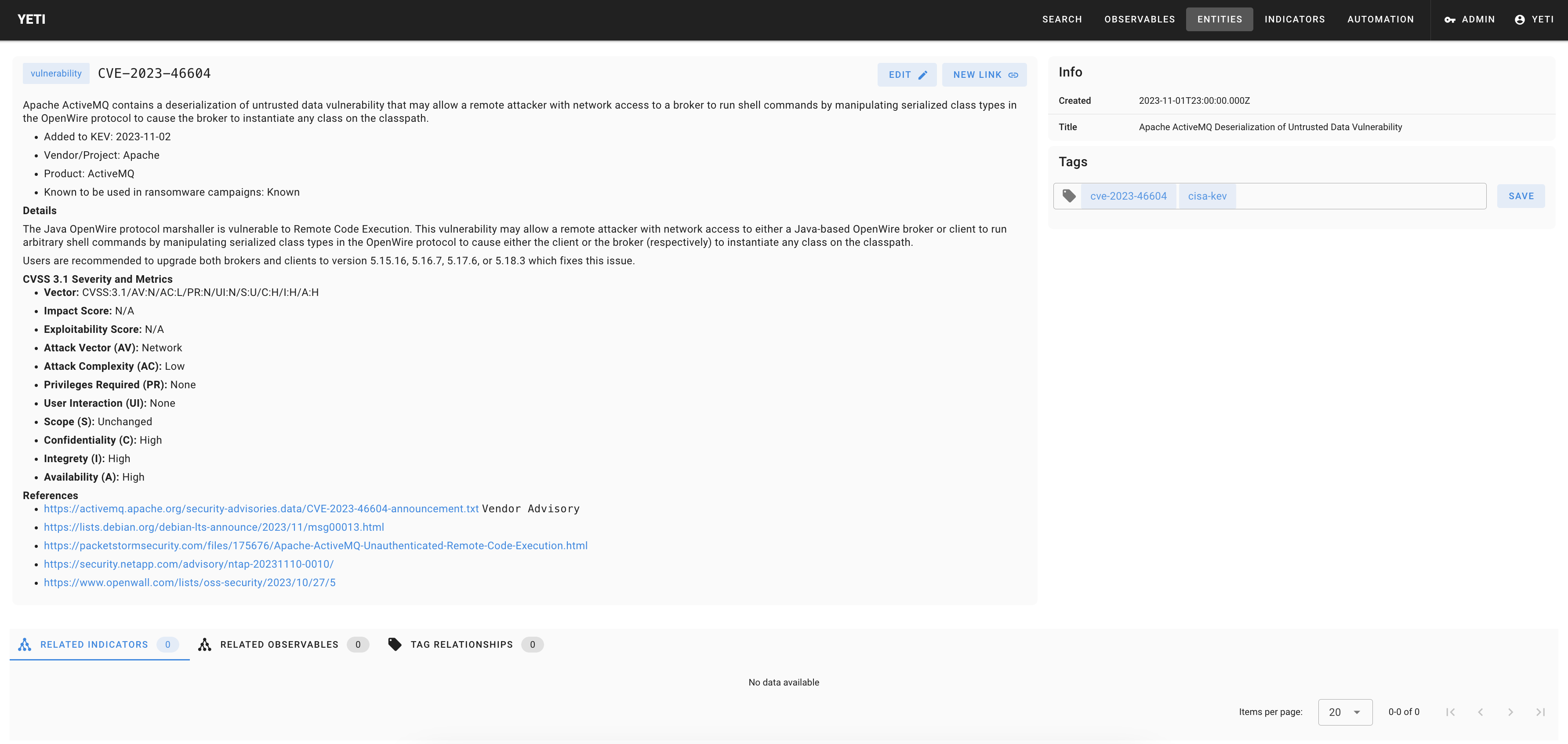
Example: CVE-2023-46604